A call upon the industry to engage more – not less! – in ASM cobalt mining.
Seven years after Amnesty International’s report “This is what we die for”, cobalt mining in the Democratic Republic of Congo (DRC) is again in the headlines, with a focus on the continuous dangers and challenges connected to artisanal cobalt mining, and with companies being pointed out for using cobalt from these mines while not doing enough to support improvement.
Cobalt is a mineral used in our Fairphone battery, and is a crucial material for the global transition to green energy, including in the electronics and automotive industries amongst others. At Fairphone, we are the first to say that the working conditions in artisanal cobalt mining in the DRC are still not acceptable, that miners are still exposed to dangers and don’t have protective equipment, and that there are still children working in hazardous and damaging environments at mine sites. In the last seven years, not sufficient progress was made in addressing these issues.
And it’s precisely because of these extreme issues that we co-founded the Fair Cobalt Alliance (FCA) in 2020. With the FCA, we choose to directly engage at the mines on the ground in DRC – because we believe we have a responsibility to invest in and contribute to improvements that are needed to positively change the conditions for these miners and their communities.
The FCA brings together industry, civil society and government and has been working to improve working conditions and health and safety at the Kamilombe mine site. The FCA also established a holistic program to address and remediate child labor in and around mine sites, and is enabling mining communities to diversify their economic opportunities.
Beyond addressing these risks and harsh conditions that are still a reality in our sectors’ supply chain, the reason why we engage with artisanal miners in the DRC is also that this sector has a huge potential to help develop the region and reduce poverty. Artisanal miners in DRC produce about 13% of cobalt globally, providing income for up to 100,000 people (depending on seasonality and commodity prices), and the DRC (combining both artisanal and industrial production) accounts for about 70% of global cobalt production in total.
But profound and lasting change won’t happen overnight.
With the FCA, we have set out to support the reform of an entire sector. There are no simple or quick solutions to formalize and improve artisanal mining. Demonizing the miners will harm rather than help because banning or excluding the most vulnerable and marginalized in our industry from global supply chains will push them out of their livelihood.
Instead, artisanal mining is a way for the local population to benefit from the increasing demand of critical minerals such as cobalt, needed for the energy transition. Artisanal cobalt miners can earn a significant income (depending on seasonality and prices), in a context where poverty is widespread and few other gainful employment opportunities are available, especially for those with little formal education or job prospects, those who have lost their land due to climate change or other land uses (including industrial mining), or those who have migrated to the area fleeing from conflict.
At Fairphone, we are therefore convinced that artisanal mining can be transformed into responsible and safe small- and medium-scale enterprises over time, creating a multiplier effect in the local economy.
So, we need to ask ourselves, as an industry: If we distance ourselves from artisanal- and small-scale miners, do we help ourselves, or do we help them? For Fairphone it is clear: we want to engage and be part of the solution, rather than disengage to have a ‘clean west’ – which we believe is akin to greenwashing.
A fair transition to an inclusive and green economy means engaging with and investing in the artisanal- and small-scale mining sector in DRC, and it means sticking to it over the long term. From the start, Fairphone’s approach has been to foster progressive improvement, to take one step after the other, to listen to and bring along everyone.
This is why things take time, and also why so much more still needs to be done: Artisanal miners need legal status and productive mine sites, expertise and infrastructure to build safer mines, protective equipment, and fair compensation for their labor. Children, youth and their families need a safe space and support to go back to school or to learn a trade that can help them provide for themselves or their families, without being exposed to the hazardous environment of a mine- and not just at one mine site, but across the sector. Communities should be able to save their earnings and invest them into health, education and economic activities, and not only bear the brunt of the negative impacts of mining.
All this can only be achieved in a multi-stakeholder effort, such as the FCA. Businesses along the cobalt value chain have a crucial role to play, and so does the government, by helping to create an enabling legal and political context. And of course civil society, to make the voices of miners and communities heard. We can only achieve a transformation of the sector if it is a joint effort with everyone making a long-term commitment. Only in this way can we make sure that the green energy transition does not lead to further exploitation of the vulnerable, and that local communities and the DRC as a country benefit.
We call upon our industry peers to engage and not look away. Collaborate, invest – and above all, listen to the producers, the miners, and their communities. If we truly want a fair transition, we have to do more and we have to do it faster.
—
You are still reading and want to know more details about Fairphone’s approach to cobalt sourcing? Here are the answers to some frequently asked questions:
- Where does Fairphone source its cobalt from?
Fairphone does not mine or source cobalt directly – rather, cobalt is used in the Fairphone’s battery. Until it gets into the battery from the mines, there are many actors, manufacturing stages and geographical locations in between: from the extraction point at the mine, cobalt typically goes to a processing plant, then a refiner, to precursor manufacturing, to cathode manufacturing, to battery cell and finally battery packaging, before the finished battery is assembled into our phone. At each of these stages, cobalt from different mines and sources is typically mixed together, making it very difficult and uneconomical to differentiate individual mines and sources. However, we know that the DRC accounts for a very large proportion of global cobalt production (74% of globally mined cobalt in 2021), and within that, artisanal sources alone amount to 13% of global production. Therefore it is safe to say that there is a high likelihood of cobalt from the DRC and from artisanal mines flowing into the electronics supply chain, including into Fairphone’s.
This is precisely why we established the Fair Cobalt Alliance – we want to engage and invest where the issues are biggest and where we can have a positive impact on the livelihoods of many thousands of people. We choose to engage and support rather than exclude and marginalize those who are already the poorest and weakest in our supply chain.
- How can Fairphone prove that its cobalt is mined ethically?
A significant share of global cobalt production, about 13%, is produced by artisanal and small-scale miners, mainly in the DRC. This cobalt is refined, mixed and processed with other sources at various stages and through that ends up in global value chains – with a high likelihood also in Fairphone’s.
This is why from the very beginning, Fairphone has been investigating how to improve the cobalt supply chain and production. Instead of turning away from DRC and artisanal miners because there are high human rights and environmental risks, we want to stay engaged on the ground and be part of a solution. ASM is a very important livelihood in DRC, and we want to help improve it and make it safer. This is why we co-founded the Fair Cobalt Alliance.
The Fair Cobalt Alliance’s work is based on an in-depth assessment of the conditions at ASM sites in DRC – this assessment was done in 2020 and published by our partner The Impact Facility here: Digging for Change. Today, the FCA works directly with an ASM cooperative on an ASM mine site in DRC. Two of the key pillars of the program is to professionalize and improve the mine site and working conditions, and to ensure that child labor is prevented and remediated in a holistic way.
Fairphone and the FCA recognize that current conditions are not acceptable and at the same time are convinced that ASM can be done in a responsible way. That is why we focus on a step-by-step continuous improvement approach and why Fairphone, together with the FCA, developed an ASM Cobalt Framework which provides Environmental, Social & Governance benchmarks to measure the progress and improvements at the mine site over time.
All of this takes time, investment and most of all, collaboration with partners on the ground. We are the first to recognize that the conditions on the ASM mine sites are not yet good. But over the course of the last two years, some first improvements have materialized. This includes the training of health and safety captains at the mine site, a system for the provision of personal protective equipment for the women cobalt washers, and establishing a health and safety committee to monitor incidents. For more detailed information on activities and progress, you can access the FCA’s quarterly and annual report here.
There is still a lot to do and many challenges and difficulties to face. And Fairphone is in it for the long term – because only with long term engagement can we get to a point where ASM cobalt production is safe and responsible.
- How does Fairphone check its supply chain of cobalt?
On an annual basis, Fairphone requests its suppliers to provide information on all the cobalt refineries in our and their supply chain. This is done by using the Extended Minerals Reporting Template (EMRT) of the Responsible Minerals Initiative (RMI), which forms part of the Responsible Business Alliance (RBA). We then analyze the data from our suppliers and check the reported refiners against the RMI’s list of certified cobalt refiners. These are refiners that are undergoing or have undergone the RMI’s Responsible Minerals Assurance Process (RMAP) – meaning they have been audited against the RMI’s Cobalt Refiner Due Diligence Standard, which certifies that the refiner has put in place the necessary measures to check, prevent and mitigate gross human rights abuses related to the sources and mines it buys from. Where we find refiners that have not yet undergone an audit, we aim to conduct outreach to convince the refiner to undergo such an audit. Where we find a refiner that has failed an audit, we aim to first engage and request improvement and only disengage from it as a last resort if no improvements are made over time. As a small company, we cannot do all of this outreach alone, and also rely on support from industry associations such as the RMI and industry peers.
We publish the list of our cobalt refiners, their location and their certification status in our Supply Chain Engagement Report, which is published annually. Here the link to the report for 2021; the report for 2022 will be published in April 2023.
- Why doesn’t Fairphone just use cobalt from other countries than the DRC?
Our goal is to stay engaged and use our buying power to drive for a positive change where improvements are most needed, instead of walking away from difficult contexts and ignoring the challenges there. Artisanal cobalt mining in the DRC is a crucial livelihood for thousands of people who have little other alternatives, due to poverty and the lack of gainful employment. We recognize that this is linked to a lot of challenges and impacts, but this is precisely why we want to engage and invest in this context. We choose to engage and support rather than exclude and marginalize those who are already the poorest and weakest in our supply chain. It is in contexts like the DRC where Fairphone can have the most positive impact.
- What does Fairphone concretely do on the ground in DRC to improve things? What has been achieved so far and what are Fairphone’s goals for its cobalt sourcing?
Fairphone engages and invests on the ground in DRC through the Fair Cobalt Alliance (FCA), which it co-founded in 2020. The FCA works directly with artisanal mining cooperatives and surrounding communities around the city of Kolwezi in DRC, where most cobalt is mined. Fairphone’s goals are aligned with the FCA’s, namely:
- to professionalize the ASM sector by investing in and supporting responsible and safe mining practices, creating dignified working conditions, and enabling fair compensation of workers
- to work towards child-labor-free communities, where the root causes of child labor are tackled in a holistic manner
- And to enable sustainable livelihoods and economic diversification of mining communities.
This year, we aim to work especially on the integration of artisanally mined cobalt into responsible supply chains, linking ASM producers with responsible markets. Ultimately we want to see an ASM sector consisting of responsible and safe small and medium-sized mining enterprises, contributing to the development of local communities and DRC as a whole.
Details about the FCA’s overall goals, its workstreams and activities, and the progress to date can be found on its website.
- Can recycled cobalt be an alternative option?
In general, using recycled materials is a first step towards a circular economy, and is therefore something Fairphone aims towards. While cobalt is recyclable in principle, and industry is using recycled cobalt already, there are a few barriers that we still encounter:
- First, until now, one of the main sources of recycled cobalt came from consumer batteries (such as in mobile phones). But due to the limited quantity and concentration of cobalt in consumer batteries, the corresponding development of recycling infrastructure to recover cobalt from such batteries has been limited. In other words, the available amount of recycled cobalt that can be re-integrated into new batteries is still small. It is not economically attractive at present, because the collection rate and the amount of cobalt are low.
- Second, the demand for electric vehicles (EV) is now growing fast, leading to enough incentive for recycling cobalt from these EV batteries. However, along with the huge demand growth driven by the green energy transition and EVs, car batteries may last 6-10 years, and only then are they expected to become a large source of recycled cobalt. And even so, there are still challenges in purification and economic feasibility for recycling cobalt from EV batteries to be used in consumer batteries (such as in Fairphone products). We are currently exploring this with our suppliers. Ultimately, researchers predict that recycled cobalt will only account for 15% of the estimated global demand in 2030. It shows that with rapidly increased demand and relatively long battery life, cobalt mining will remain relevant and in need of our attention.
- Thirdly, collecting more waste consumer batteries is surely an option. But batteries are classified as a hazardous good and therefore their transport, storage and handling are subject to strict safeguards and standards. This is why our take-back program of e-waste from informal waste dumps in Africa with our partners Closing The Loop does not yet cover batteries.
Overall, we are exploring the use of recycled cobalt in our batteries when and where we can, but we also see the need to accompany this with two other measures: 1) Engage in improving mining, because we will remain dependent on mined sources for some time, and 2) contribute to improving recycling rates of batteries.
The post Sticking with Cobalt Blue appeared first on Fairphone.





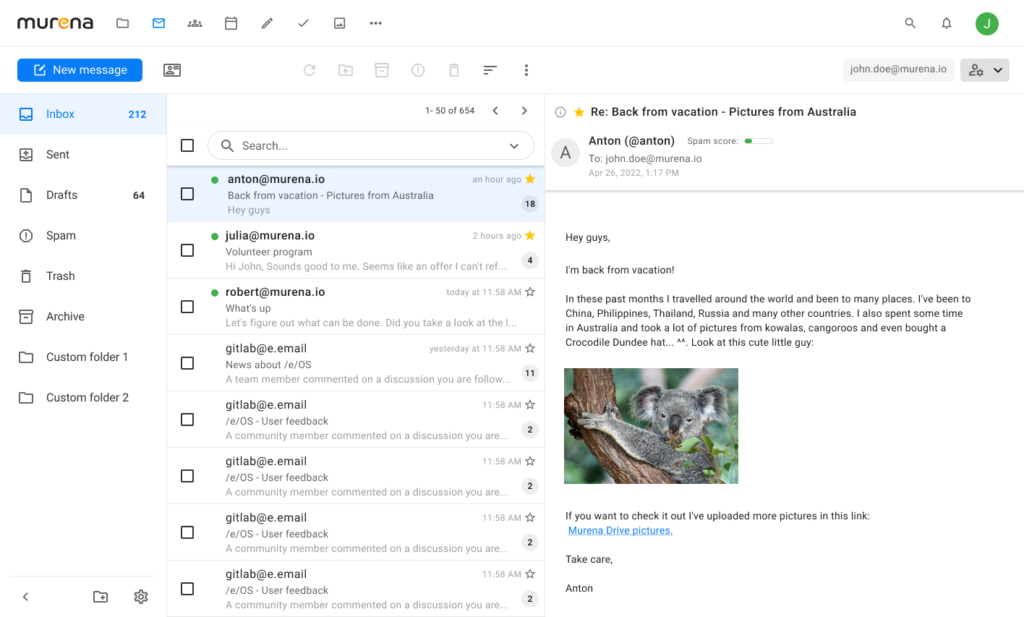
 The new tab entries used to be in the middle.
The new tab entries used to be in the middle. They have now been moved to the top.
They have now been moved to the top.
 We see you searching for "Best 1863 songs of all time".
We see you searching for "Best 1863 songs of all time".
 What? It's good music. Shut up.
What? It's good music. Shut up.
 Fits perfectly with "What's New" now being a default tab on the main page.
Fits perfectly with "What's New" now being a default tab on the main page.
 Sonic will rage for 1 and a 1/2 hours.
Sonic will rage for 1 and a 1/2 hours.
 Yes, we are totally up to date with Android versions!
Yes, we are totally up to date with Android versions!
 You can't count the pixels anymore, even if you try!
You can't count the pixels anymore, even if you try!
 We are an open book. (This joke wrote itself.)
We are an open book. (This joke wrote itself.)

 If you want that effect now, you can put paper in front of your TV.
If you want that effect now, you can put paper in front of your TV.





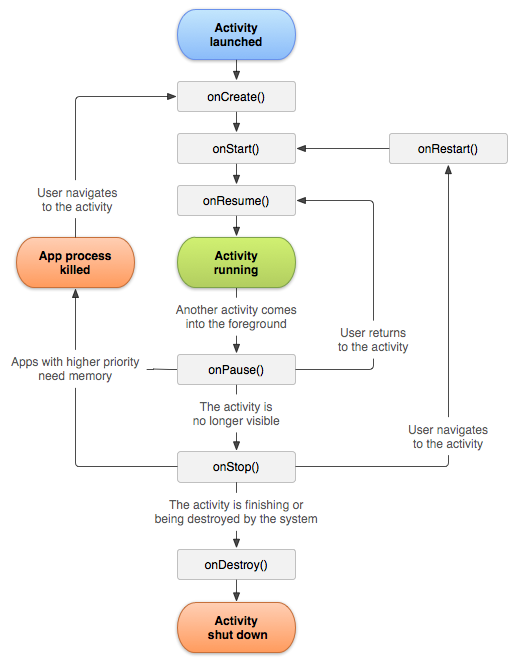 Believe it or not, this chart represents a simplified model of what really goes down.
Believe it or not, this chart represents a simplified model of what really goes down. They make sure to let you know that this is a simplified representation.
They make sure to let you know that this is a simplified representation. Cute kids! Also, some people like icons that are all the same color.
Cute kids! Also, some people like icons that are all the same color.
 Board members
and community observers attend the virtual singing of the board statutes.
Board members
and community observers attend the virtual singing of the board statutes.


 Open to me the secrets of the WebView!
Open to me the secrets of the WebView! Begone!
Begone! That doesn’t even sound grammatically correct.
That doesn’t even sound grammatically correct. Everybody keep your hands to yourself!
Everybody keep your hands to yourself!